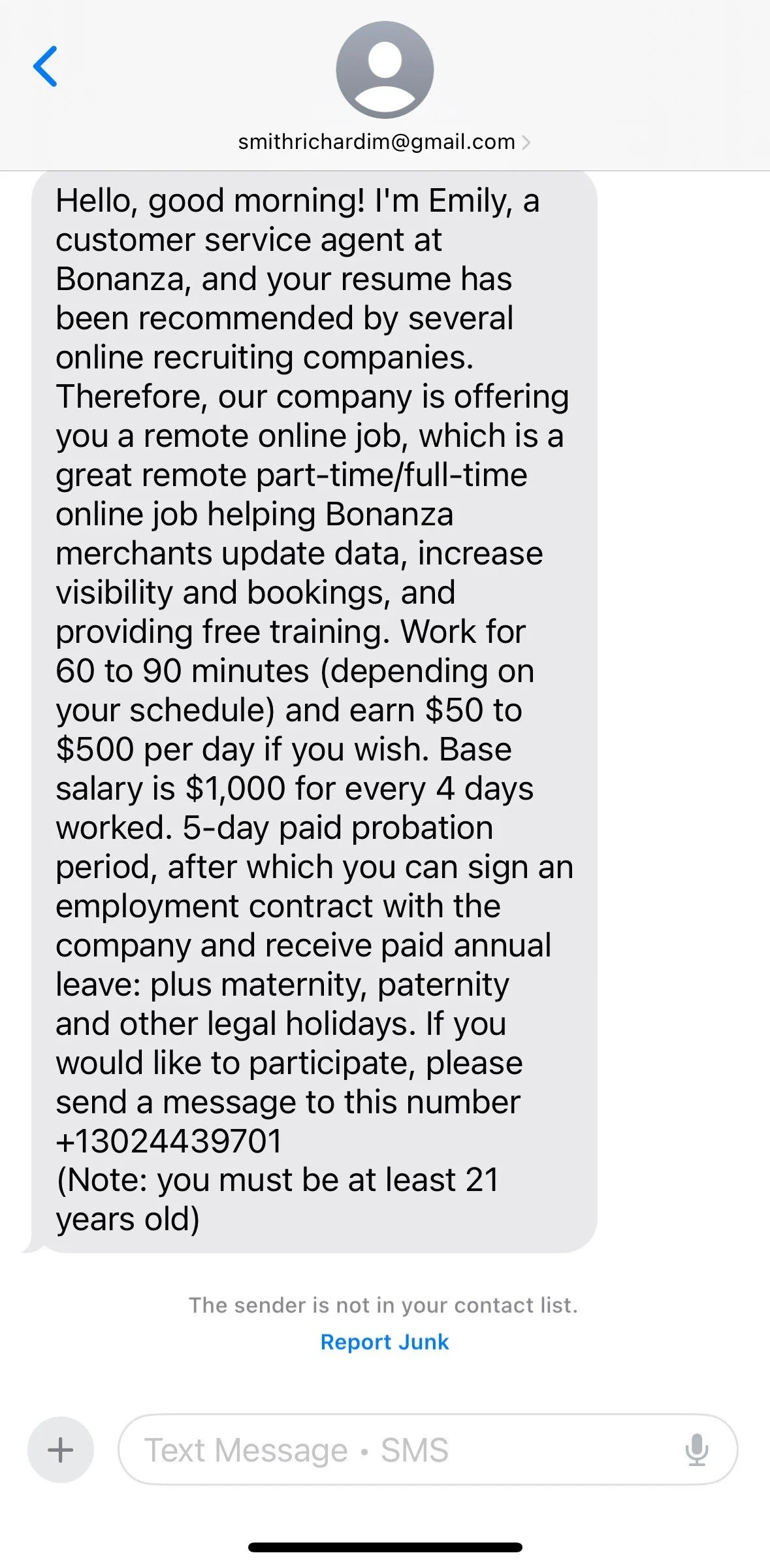
In today's job market, the allure of remote work has become increasingly enticing. However, companies have started to shift away from remote work post-pandemic and are requiring more in-person or hybrid for employees. Combine that with the downsizing companies are going through at this time and job scams are going to pop up on a more regular basis. Recently, I got the above text from a “recruiter.”
While this might seem like a great opportunity it’s a scam. A job offer does not typically come over text nor does it happen without an interview. This is a path to getting personal information, financial, or drawn into the scam ecosystem as a money mule.
The Scam: Too Good to Be True
The scam typically begins with an unsolicited message from an individual claiming to be "Emily," a customer service agent at Bonanza. The message outlines an attractive remote position with the following promises:
High Earnings: Potential to earn between $50 to $500 per day, with a base salary of $1,000 for every four days worked.
Flexible Hours: Commitment of just 60 to 90 minutes per day.
Comprehensive Benefits: Offers include paid annual leave, maternity and paternity leave, and other legal holidays.
Minimal Effort: Assurances of free training and a guaranteed paid probation period.
Recipients are encouraged to respond to a provided phone number to seize this "opportunity."
Red Flags in the Offer
While the proposition may appear appealing, several indicators suggest it's a scam:
Unsolicited Contact: Legitimate companies seldom extend job offers without prior interaction or application. Receiving such a message without prior engagement is suspicious.
Free Email Account: This text was sent with a Gmail account that anyone that is available to anyone for free.
Exaggerated Earnings and Benefits: Promises of substantial income for minimal work are classic red flags. Genuine employers provide realistic compensation aligned with industry standards.
Vague Job Description: The lack of specific details about job responsibilities, using ambiguous phrases like "helping merchants update data," is a common tactic to obscure the scam's true nature.
Urgency to Respond: Scammers often create a sense of urgency to prevent thorough consideration. Pressuring immediate action is a tactic to catch victims off-guard.
Unprofessional Communication: Errors in grammar, informal language, or inconsistencies in the message are telltale signs of fraudulent communication.
Request for Contact via Personal Number: Legitimate companies typically use official communication channels. Requests to contact personal numbers are uncommon and suspicious.
What Happens If You Respond?
Engaging with the scammer can lead to several detrimental outcomes:
Phishing for Personal Information: Scammers may request sensitive data, such as Social Security numbers or banking details, under the guise of processing employment paperwork.
Upfront Payments: Requests for fees covering "training" or "equipment," with promises of reimbursement, are common. Once paid, these funds are unrecoverable.
Identity Theft: Shared personal information can be exploited for identity theft, leading to financial and legal complications.
No Real Job: After extracting money or information, the scammer disappears, leaving the victim without employment and at a loss.
Become a Money Mule: A money mule is someone who transfers or moves illegally acquired money on behalf of others, often unknowingly.
Protecting Yourself from Job Scams
To shield yourself from such fraudulent schemes, consider the following precautions:
Research the Company: Visit the official website and verify job postings. Authentic opportunities are listed on company websites or reputable job boards.
Verify the Contact: Ensure that communications come from official company channels. Be wary of contacts using personal email addresses or phone numbers.
Be Skeptical of Extravagant Claims: If an offer seems too good to be true, it warrants skepticism. Legitimate jobs have clear expectations and reasonable compensation.
Never Pay to Work: Authentic employers do not require upfront payments for any reason.
Report Suspicious Offers: Report potential scams to the Federal Trade Commission (FTC) at ReportFraud.ftc.gov and to the platform where the offer was encountered.
Conclusion
Scammers continually adapt their tactics to exploit the evolving job market and technological landscape. By staying informed and vigilant, you can protect yourself from falling victim to such schemes. Always verify the legitimacy of job offers and remain cautious of unsolicited communications. Remember, if something feels amiss, it's worth investigating further. Stay safe and informed in your job search and digital interactions.