This is a newsletter I create and share with my internal security team. Feel free to grab and do the same.
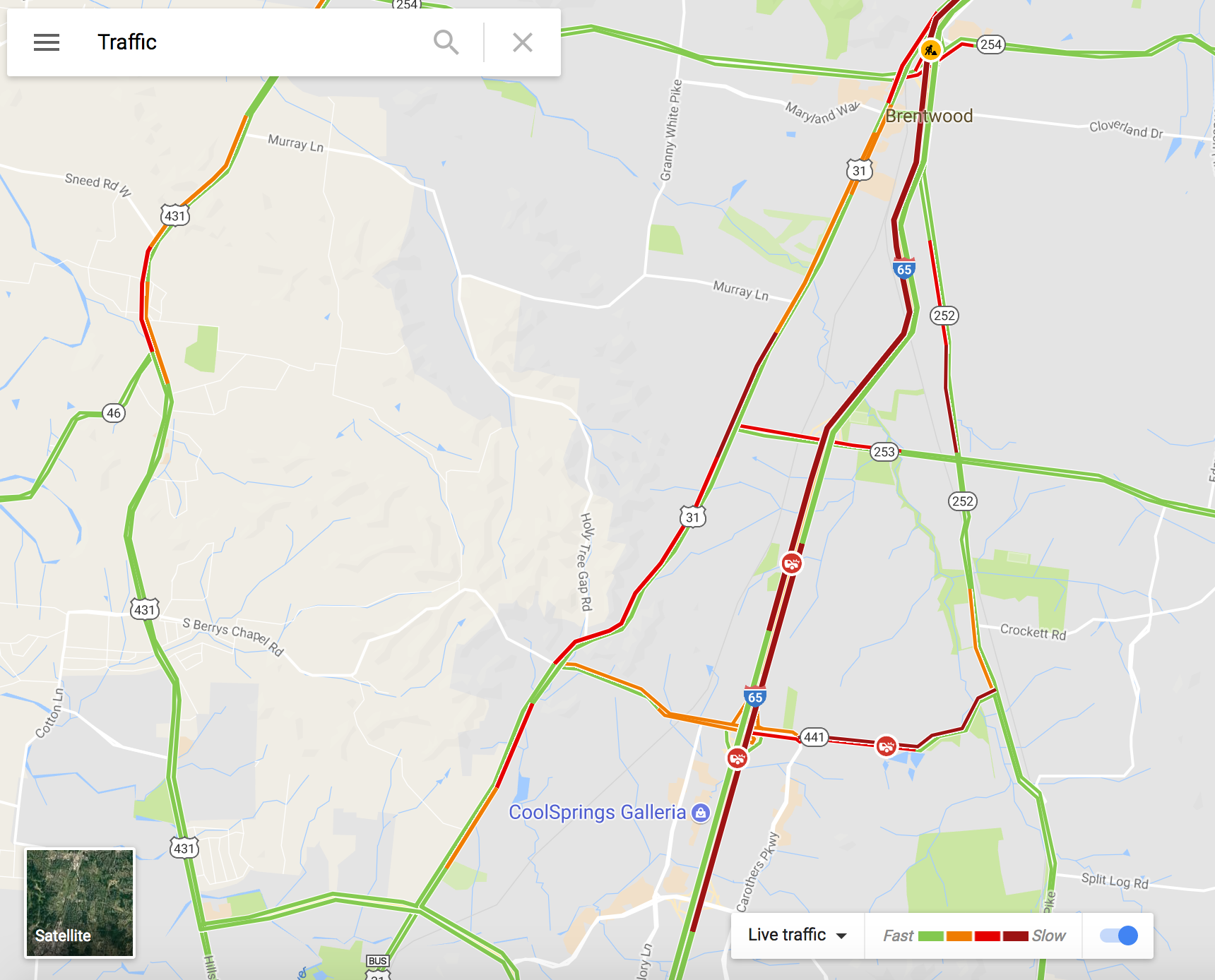
Ransomware Ecosystem in Flux
Coveware's latest analysis reveals a significant transformation in the ransomware threat landscape as of Q1 2025. The once-dominant Ransomware-as-a-Service (RaaS) model is unraveling due to intensified law enforcement actions, internal discord, and operational setbacks.
Key Insights:
Disintegration of Major RaaS Groups: Prominent groups like LockBit, BlackCat/ALPHV, and Black Basta have collapsed, plagued by internal conflicts and increased scrutiny. Leaked communications from Black Basta highlight challenges in targeting, risk assessment, and evasion of sanctions.
Emergence of New Threat Actors: The void left by these groups is being filled by unaffiliated extortionists, nascent ransomware brands with ties to espionage and hacktivism, and a few remnants of traditional ransomware operations.
Operational Missteps: Recent incidents, such as Clop's underwhelming Cleo campaign and a poorly executed Oracle Cloud SSO breach by a BreachForums actor, indicate a decline in the sophistication and monetization strategies of threat actors.
Further Reading: Coveware
Stealthy .NET Malware: Hiding Malicious Payloads as Bitmap Resources
Unit 42 researchers have identified a novel obfuscation technique employed by threat actors, wherein malicious payloads are concealed within bitmap resources embedded in seemingly benign 32-bit .NET applications. This method leverages steganography to initiate a multi-stage execution chain, ultimately deploying final payloads such as Agent Tesla, RemcosRAT, or XLoader.
Key Insights:
Further Reading: Unit 42
New Tool Can Trick Windows into Disabling Microsoft Defender
Security researchers have discovered a new, publicly available tool called "DefendNot" that can manipulate Windows systems into effectively disabling Microsoft Defender, the built-in antivirus software. This tool doesn't exploit vulnerabilities but instead uses legitimate system administration features in unintended ways.
Key Insights for Security Teams:
Further Reading: BleepingComputer
NIST Proposes Metric to Identify Likely Exploited Vulnerabilities
The National Institute of Standards and Technology (NIST), in collaboration with the Cybersecurity and Infrastructure Security Agency (CISA), has introduced a proposed metric aimed at determining the likelihood that a given vulnerability has been exploited in the wild. This initiative seeks to enhance the efficiency and cost-effectiveness of enterprise vulnerability remediation efforts.
Key Insights:
Addressing Limitations of Existing Systems: Current remediation strategies often rely on the Exploit Prediction Scoring System (EPSS) and Known Exploited Vulnerabilities (KEV) lists. However, EPSS has been noted for inaccuracies, and KEV lists may not be comprehensive. The proposed metric aims to augment these tools by providing a more accurate assessment of exploitation likelihood.
Further Reading: NIST CSWP 41
New Best Practices Guide for Securing AI Data Released
CISA, NSA, FBI, and international partners have jointly released a new Cybersecurity Information Sheet focused on AI Data Security: Best Practices for Securing Data Used to Train & Operate AI Systems. This guide emphasizes that robust data security is fundamental for ensuring the accuracy, integrity, and trustworthiness of AI outcomes throughout its entire lifecycle.
Key Insights:
Target Audience: It's particularly relevant for Defense Industrial Bases, National Security Systems owners, federal agencies, and Critical Infrastructure owners/operators.
Core Recommendations: Key practices include adopting strong data protection measures, proactively managing AI-related risks, and enhancing monitoring, threat detection, and network defense capabilities.
Further Reading: CISA
DDoS Attack "Street Prices": What You Need to Know
Recent analysis of the underground market reveals that the "street prices" for DDoS (Distributed Denial-of-Service) attacks have remained remarkably stable over the past few years, with some new trends in service delivery. While web-based booters are still available, Telegram-based booter services are becoming a new norm, offering readily accessible attack capabilities.
Key Insights:
DDoS-as-a-Service (DDoSaaS) Dominance: This business model continues to thrive, with attackers charging hourly or monthly fees to sustain attacks, often with extra charges for targeting protected services.
Further Reading: KyberVandals Blog
Deceptive CAPTCHA "ClickFix" Campaign Uses Clipboard Injection to Deliver Malware
Threat actors are employing a new social engineering campaign, dubbed "ClickFix," that utilizes fake CAPTCHA prompts on compromised or cloned websites. This sophisticated technique tricks users into launching malware by combining clipboard injection with abuse of the Windows Run dialog, leading to the delivery of payloads like Lumma Stealer and NetSupport RAT.
Key Insights:
Living Off the Land Binaries (LOLBins): Attackers extensively use trusted system binaries like PowerShell, mshta.exe, and certutil.exe to bypass traditional security defenses, making detection challenging.
Payloads: Frequently observed payloads include infostealers (e.g., Lumma Stealer targeting browser data, credentials, and crypto wallets) and remote access tools (e.g., NetSupport RAT for full system access).
Further Reading: SecurityOnline.info
Cybercriminals Exploit AI Hype to Spread Malware
Cybercriminals are increasingly exploiting the public's interest in artificial intelligence by creating fake AI-themed websites and advertisements to distribute malware. A recent campaign identified by Mandiant Threat Defense involves the threat group UNC6032 using deceptive ads on platforms like Facebook and LinkedIn to lure users into downloading malicious software disguised as AI video generation tools.
Key Insights:
Malware Deployment: Upon interacting with these fake sites, users are prompted to download a ZIP file containing the STARKVEIL malware dropper. This dropper installs multiple malware components, including GRIMPULL, XWORM, and FROSTRIFT, which are designed to steal sensitive information and establish persistent access to the victim's system.
Information Theft: The deployed malware targets a range of data, including login credentials, cookies, credit card information, and digital wallet contents. Some components, like XWORM, also perform keylogging and screen capture, further compromising user privacy.
This campaign underscores the importance of vigilance when engaging with online advertisements, especially those offering AI-related services. Users should be cautious of unsolicited offers and verify the legitimacy of websites before downloading any software.
Further Reading: Google Cloud Blog
Beyond the Kill Chain: How Cybercriminals Invest Their Profits
Sophos X-Ops' five-part series, Beyond the Kill Chain, explores what happens after a successful cyberattack. The series reveals how financially motivated threat actors invest their illicit earnings—often blending legitimate business with ethically questionable and outright criminal ventures.
Key Insights:
Legitimate Business Ventures: Cybercriminals are investing in seemingly lawful enterprises such as restaurants, real estate, and e-commerce platforms. These ventures help launder money while also creating additional income streams.
Ethically Dubious Activities: Some threat actors operate in legal gray zones, selling spyware, monetizing vulnerability research under the guise of security services, or manipulating online traffic for advertising profits.
Criminal Enterprises: Illicit gains are also funneled into traditional criminal operations like counterfeit goods, drug trafficking, and underground gambling, showing how cybercrime supports broader organized crime ecosystems.
Further Reading: Sophos News
Lumma Infostealer: Disrupted but Not Defeated
A recent global law enforcement operation disrupted parts of the Lumma Infostealer malware-as-a-service platform, seizing over 2,500 domains. However, key infrastructure—particularly servers hosted in Russia—remains intact, allowing Lumma’s core operations to continue.
Key Insights:
Further Reading: Check Point Blog
CFOs Targeted in Sophisticated Spear-Phishing Campaign
A recent spear-phishing campaign is targeting Chief Financial Officers (CFOs) and finance executives across banking, energy, insurance, and investment sectors in regions including Europe, Africa, Canada, the Middle East, and South Asia. The attackers use a multi-stage approach to deploy NetBird, a legitimate WireGuard-based remote access tool, onto compromised systems.
Key Insights:
Malicious Payload Delivery: After solving the CAPTCHA, users download a ZIP file containing a VBS script. When executed, it installs NetBird and OpenSSH, creates a hidden local admin account, and enables Remote Desktop Protocol (RDP) for persistent attacker access.
Further Reading: Trellix Blog
Threat Actors Exploit Google Apps Script for Evasive Phishing Attacks
Threat actors are leveraging Google's Apps Script platform to host phishing pages that appear legitimate, allowing them to steal login credentials. These campaigns often begin with emails posing as invoice notifications, linking to webpages hosted using Google Apps Script. By operating within Google's trusted environment, attackers make their phishing pages seem more authentic, increasing the chances of success.
Key Insights:
Abuse of Trusted Services: Google Apps Script, a JavaScript-based platform used for automating Google Workspace tasks, is being exploited to host fake login pages that capture user credentials and send them to attacker-controlled servers.
Further Reading: BleepingComputer
HuluCAPTCHA – An Evolving Fake CAPTCHA Framework
Security researchers have identified "HuluCAPTCHA," a sophisticated fake CAPTCHA framework actively compromising websites. This advanced system tricks users into running malicious commands via fake CAPTCHA prompts and the Windows Run dialog, leading to infections with infostealers and remote access tools.
Key Insights:
Payload Versatility: Delivers various infostealers (e.g., Lumma, Aurotun) and remote access tools (e.g., Donut Injector).
Further Reading: HuluCaptcha — An example of a FakeCaptcha framework
Phishing Campaign Exploits Google.com Open Redirects
A recent phishing campaign has been observed exploiting an open redirect vulnerability within Google's google.com/travel/clk endpoint. Threat actors are leveraging this legitimate Google Travel click-tracking mechanism to redirect users from a trusted google.com domain to malicious phishing sites. This technique adds an air of legitimacy to phishing links, making them harder for users to identify as fraudulent.
Key Insights:
Persistent Tokens: The pc token, which controls the redirect, lacks a clear expiration mechanism and can remain valid for months or even years. This allows attackers to reuse tokens across multiple campaigns.
Mitigation Recommendation for Internal Security Teams:
Further Reading: Another day, another phishing campaign abusing google.com open redirects
Cybercriminals Use Fake Booking Sites to Spread AsyncRAT Malware
Cybercriminals are exploiting fake Booking.com websites to infect users with AsyncRAT, a remote access trojan. Victims are lured through deceptive ads and social media links to counterfeit booking sites, where they are tricked into running a malicious PowerShell script. The attack results in full remote control of the infected system, putting sensitive personal information at risk.
Key Insights:
Further Reading: Malwarebytes Blog
UNC6040 – Voice Phishing to Salesforce Data Extortion
Google Threat Intelligence Group (GTIG) is tracking UNC6040, a financially motivated threat cluster specializing in voice phishing (vishing) campaigns. This group is successfully impersonating IT support to gain access to organizations' Salesforce instances, primarily to steal large volumes of data for subsequent extortion. Their tactics rely heavily on manipulating end users rather than exploiting software vulnerabilities.
Key Insights:
Further Reading: The Cost of a Call: From Voice Phishing to Data Extortion