This is a monthly newsletter I put together for our internal security team with a lean towards phishing and healthcare. Created with help from ChatGPT.
Fake Job Applications Deliver Dangerous Malware
Summary: A spear-phishing campaign is targeting HR professionals with fake job applications containing the More_eggs malware. Operated by the Golden Chickens group as part of a Malware-as-a-Service (MaaS) platform, More_eggs is a sophisticated backdoor used by multiple threat actors to infiltrate corporate networks.
Key Insights (Technical):
For further details, read the full article on The Hacker News.
New Ransomware Strain Targeting Healthcare
The U.S. Department of Health and Human Services (HHS) issued a warning about a new ransomware strain, Trinity, which is actively targeting the healthcare sector. Trinity uses techniques like encrypting data and demanding ransoms within 24 hours. It has connections to other ransomware families such as Venus and 2023Lock.
Technical Key Insights:
Further reading: The Record - Trinity Ransomware Alert.
Emerging Cybersecurity Threats Highlighted in HP Wolf Security Report
The September 2024 HP Wolf Security Threat Insights Report identifies key trends in cyberattacks, including a surge in document-based malware, with 61% of threats delivered via email attachments. Attackers are increasingly using malicious archives and PDFs to bypass detection, leveraging techniques like HTML smuggling and exploiting vulnerabilities in outdated software. Threat actors are also using Generative AI to write sophisticated malware, such as AsyncRAT.
Key Insights:
Further reading: HP Wolf Security Threat Insights Report.
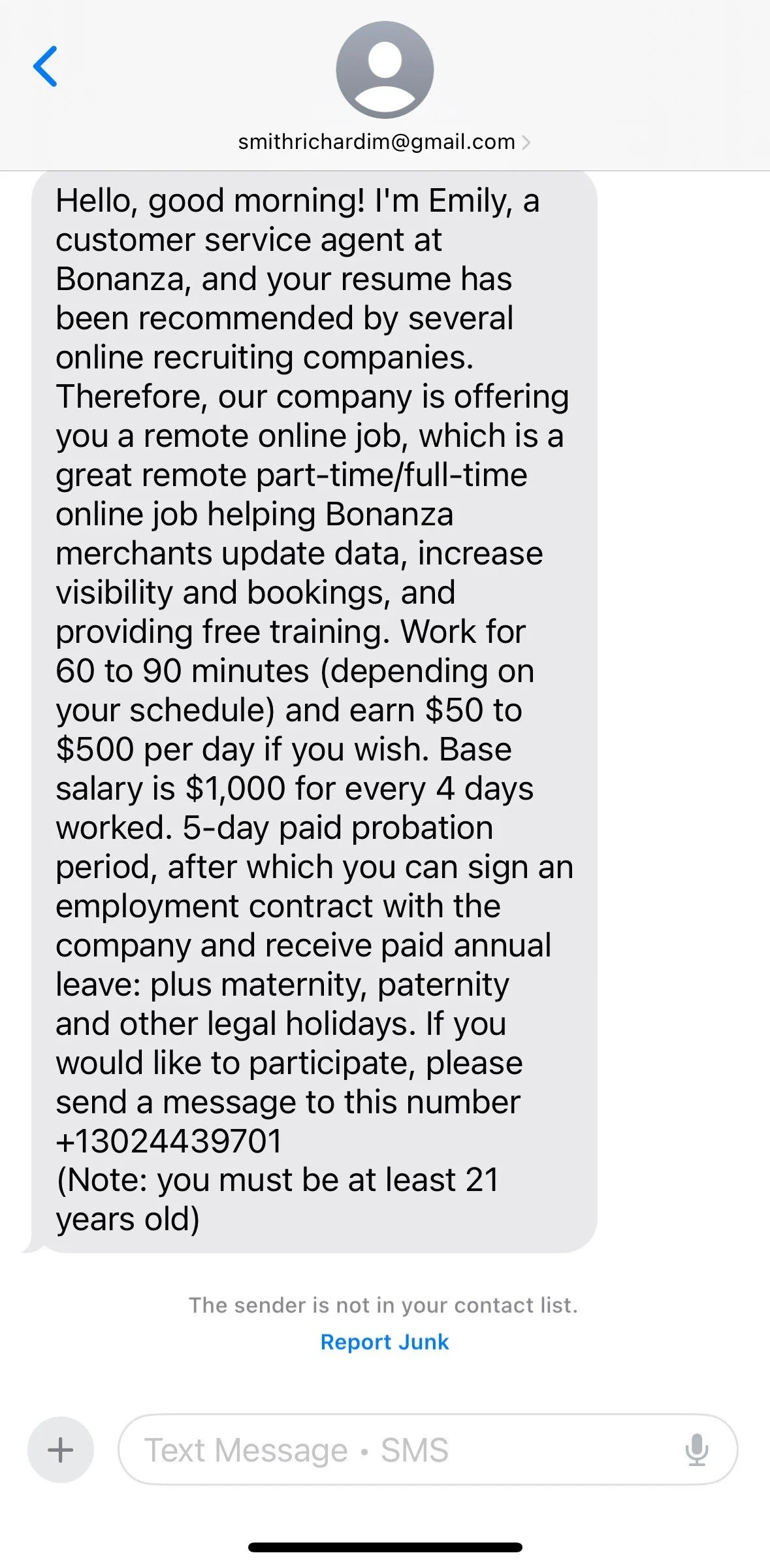
North Korean IT Worker Incident Highlights Hiring Risks
A recent cyberattack on a company underscores the dangers of unknowingly hiring North Korean operatives. The organization accidentally hired a North Korean IT worker who accessed sensitive data and demanded a ransom. This highlights the need for stringent vetting in remote hiring practices, especially as North Korea increasingly infiltrates global companies.
Recommended Protections:
Further reading: GBHackers - North Korean IT Worker Incident.
User-Centric Security Design Inspired by Disney
A recent article from KnowBe4 discusses how organizations can improve security by observing how employees naturally work, similar to Disney’s strategy of observing guests before building paths. The concept of "desire paths" shows that security controls should be designed around actual workflows, reducing friction and improving compliance. By aligning security with user behavior, organizations can mitigate risky workarounds and foster a more secure environment.
Further reading: KnowBe4 - Security Highways.
Healthcare Supply Chain Attacks on the Rise
A recent Proofpoint report reveals that 68% of healthcare workers have faced a supply chain cyberattack, with 82% of these incidents affecting patient care.
Key Insights:
Further reading: Security Magazine - Supply Chain Attacks.
Microsoft’s Deceptive Honeypot Strategy Targets Phishers
Microsoft has launched a clever security strategy by creating fake Azure tenants to lure phishing attackers into honeypots. These realistic tenant environments mimic legitimate setups, tricking attackers into interacting with them. This allows Microsoft to gather valuable intelligence on phishing methods and infrastructure, which can be used to strengthen defenses and share with the wider security community. By engaging with these fake environments, phishers waste time while Microsoft gains crucial insights.
Further reading: BleepingComputer - Microsoft Honeypots.
Mobile-First Cyber Attacks on the Rise
Cyber attackers are increasingly adopting a "mobile-first" strategy, as highlighted by a new report from Zimperium. With 83% of phishing sites now targeting mobile devices and a 13% rise in mobile malware, employees’ personal devices pose a growing risk to organizations. As more employees use their smartphones for work-related tasks, organizations need to bolster mobile security and educate employees on safe practices through security awareness training.
Further reading: KnowBe4 - Mobile-First Attack Strategy.
Cybercriminals Exploiting Steam for Malware Distribution
A recent investigation highlights how cybercriminals are using Steam profiles to exploit a technique called Dead Drop Resolver (DDR) to hide Command and Control (C2) addresses within user profiles. Attackers have leveraged well-known infostealers like Vidar, Lumma, and MetaStealer to extract sensitive data from infected systems by using platforms like Steam and Telegram to evade detection.
Technical Key Insights:
Further reading: RT Solar Blog. <---- .ru site
Rise in Phishing Attacks with AI and Impersonation Tactics
A new report from KnowBe4 reveals a 28% rise in phishing attacks during Q2 2024, with 89% of attacks involving brand impersonation. Cybercriminals are increasingly using AI-powered phishing toolkits, making it easier for less-skilled attackers to execute sophisticated campaigns. Commodity phishing attacks, primarily using hyperlinks, have surged, overwhelming organizations' defenses. With impersonation tactics being a dominant trend, organizations must enhance defenses against these evolving threats.
Key Insights:
Further reading: KnowBe4 Report.
Phishing-as-a-Service Platform "Sniper Dz" Exposed
A recent investigation reveals the rise of the phishing-as-a-service (PhaaS) platform "Sniper Dz," which is responsible for over 140,000 phishing websites. The platform offers phishing templates targeting major brands and hides malicious content behind proxy servers to evade detection. Additionally, attackers can exfiltrate credentials to centralized servers controlled by Sniper Dz. This growing platform enables less-skilled attackers to launch sophisticated phishing attacks with ease.
Further reading: Unit 42 - Sniper Dz PhaaS.
Dark Angels Ransomware Group Exposed
A recent investigation uncovers the stealth tactics of the Dark Angels ransomware group, which targets high-value systems with Babuk and RagnarLocker-based ransomware. Their techniques include double extortion, data exfiltration, and selective ransomware deployment to minimize detection.
Technical Key Insights:
Further reading: Zscaler - Dark Angels Ransomware Group.
North Korean IT Worker Fraud
SecureWorks reports that North Korean IT workers are fraudulently obtaining remote jobs to access sensitive systems and generate revenue for the regime. These individuals disguise their identities, use VPNs to hide their location, and exploit company resources once hired.
Key Insights:
Further Reading: Fraudulent North Korean IT Worker Schemes
Health Care and Social Assistance Sector at Risk
Cyber threats in the Health Care and Social Assistance sector are intensifying, with phishing and social engineering attacks being the most prevalent. Organizations need to prioritize automation and Digital Risk Protection strategies to defend against these sophisticated threats.
Key Insights:
Further Reading: ReliaQuest Health Care Threat Landscape
AI-Driven Malware and Persistent Ransomware Threats
Check Point's Global Threat Index for September 2024 highlights the rising use of AI in malware creation, with AsyncRAT becoming one of the top threats. AI-powered scripts are being used to deliver malware like AsyncRAT through techniques such as HTML smuggling, showcasing how threat actors with limited technical skills can now leverage AI to create sophisticated attacks. This evolution underscores the need for organizations to adopt proactive security strategies.
In addition, RansomHub, a rebranded Ransomware-as-a-Service group, continues to dominate the ransomware scene, accounting for 17% of reported attacks. Other prominent malware families include FakeUpdates, targeting organizations worldwide, and Androxgh0st, which exploits vulnerabilities across platforms.
Key Insights:
Further Reading: Check Point Threat Intelligence Report
Trinity Ransomware Hits Healthcare Sector
The Trinity ransomware group is targeting healthcare organizations with double-extortion tactics, gaining access through phishing emails and software vulnerabilities. This ransomware not only encrypts data but also steals it, pressuring victims to pay or risk exposure of sensitive information. Two healthcare providers have already been attacked, with 330GB of data compromised from a U.S.-based provider.
Key Insights:
Further Reading: Trinity Ransomware Targets Healthcare
Threat Intelligence Update: Black Basta’s Social Engineering Tactics via Microsoft Teams
The Black Basta ransomware group has employed a sophisticated social engineering campaign targeting organizations through Microsoft Teams. By signing user emails up for multiple spam sources, Black Basta overwhelms the target with unwanted messages. Threat actors then contact the user, impersonating IT support and offering assistance with the email flood. During this call, the attacker convinces the user to install remote access software like Quick Assist or AnyDesk, providing them unauthorized access to the network. Once inside, the attackers can harvest credentials and potentially deploy ransomware.
Key Insights:
Further Reading: ReliaQuest Blog on Black Basta's Techniques
Q3 2024 Ransomware Trends
The ReliaQuest Q3 2024 ransomware report highlights significant shifts in the ransomware landscape, with new groups gaining prominence and using sophisticated tactics to escalate their attacks. RansomHub has overtaken LockBit as the most active group, experiencing an 800% rise in postings from Q1 to Q3. Their growth is attributed to aggressive recruiting and lucrative profit-sharing, which has drawn affiliates from other disrupted groups. This group, along with Play ransomware, continues to exploit vulnerabilities in VPNs and public-facing applications, demonstrating the persistent risk posed by unpatched systems.
Key Insights:
Further Reading: ReliaQuest Q3 Ransomware Report
Update: Q3 2024 Brand Phishing Trends
Check Point Research’s Q3 2024 report reveals that Microsoft continues as the most impersonated brand in phishing attacks, accounting for 61% of brand phishing attempts. Apple (12%) and Google (7%) follow, with new additions Alibaba and Adobe rounding out the top 10. These attacks commonly target the technology, social media, and banking sectors, as cybercriminals exploit brand familiarity to deceive users and capture credentials or payment information. Notably, new phishing sites targeting WhatsApp and Alibaba highlight the evolving strategies of threat actors seeking to exploit user trust.
Key Insights:
Further Reading: Check Point’s Q3 2024 Brand Phishing Report.
Global Surge in Cyber Attacks in Q3 2024
Check Point’s Q3 2024 report highlights a significant 75% increase in global cyber attacks compared to last year, with each organization facing an average of 1,876 weekly attacks. Sectors most impacted include Education/Research (3,828 weekly attacks), Government/Military (2,553), and Healthcare (2,434), reflecting the increased focus on these industries. Africa saw the highest regional attack rate, averaging 3,370 weekly, up 90% from 2023, while North America experienced the most ransomware attacks, making up 57% of incidents worldwide. Manufacturing was the top ransomware target, followed by Healthcare and Retail/Wholesale.
Key Insights:
Regional Hotspots: Africa, Latin America, and Europe saw the steepest rises, with Europe experiencing an 86% year-over-year spike.
Further Reading: Check Point Q3 2024 Report.
North Korean Cybercriminal Infiltrates UK Company
A UK-based organization recently suffered a breach after inadvertently hiring a North Korean cybercriminal posing as a remote IT worker. Once hired, the attacker used insider access to extract sensitive information and eventually demanded a ransom for its non-disclosure. This case highlights the importance of strict hiring processes for remote roles and enhanced security practices.
Key Insights:
Further Reading: KnowBe4 Article; KnowBe4 10 Hiring Updates
Partnership Between Scattered Spider and RansomHub
ReliaQuest reports a new collaboration between the Scattered Spider and RansomHub groups, merging advanced social engineering skills with network-compromising expertise to target enterprises globally. The partnership leverages RansomHub's effective 90/10 profit-sharing model, attracting experienced threat actors from disrupted groups. This collaboration allows attackers to target critical virtual infrastructures, such as ESXi servers, which host key applications, enabling high-impact ransomware attacks that pressure victims to pay swiftly.
Key Insights:
For more details, explore the full article at ReliaQuest.
Social Engineering Exploits Valid Accounts
Recent incidents highlight how threat actors are compromising legitimate accounts through social engineering tactics. By manipulating individuals into divulging sensitive information or performing specific actions, attackers gain unauthorized access to systems and data. This method often involves impersonating trusted entities or creating convincing scenarios to deceive targets.
Key Insights:
Further Reading: KnowBe4 Article on Social Engineering Exploits.
North Korean Group Adopts Play Ransomware
Unit 42 has identified that the North Korean state-sponsored threat group, Jumpy Pisces (also known as Andariel), has begun collaborating with the Play ransomware group, Fiddling Scorpius. This marks a significant shift in Jumpy Pisces' tactics, moving from traditional cyber espionage to active participation in ransomware operations. The group gained initial access to networks via compromised user accounts, deploying tools like Sliver and their custom malware, DTrack, to facilitate lateral movement and persistence. This collaboration underscores the evolving ransomware landscape, where nation-state actors are increasingly engaging in financially motivated cybercrime.
Key Insights:
Further Reading: Unit 42 Article on Jumpy Pisces and Play Ransomware.
Key Cyber Threat Actors in 2024
ReliaQuest's recent analysis identifies five prominent cyber threat actors significantly impacting the cybersecurity landscape in 2024:
APT41: A Chinese state-affiliated group, APT41 continues to engage in espionage activities, targeting sectors such as healthcare, telecommunications, and finance.
Further Reading: ReliaQuest Article on Critical Threat Actors.
Halloween’s Digital Threats of 2024
Halloween brings tales of horror, but in 2024, some of the scariest threats come from the digital realm. Cybercriminals are increasingly using advanced tools to target individuals and organizations with new forms of AI-driven malware, IoT exploits, and social engineering tricks that play on our trust.
Key Insights:
IoT Vulnerabilities: Over 20,000 vulnerable IoT devices, including cameras and routers, have become entry points for attackers, posing risks to privacy and security.
Further Reading: Check Point’s guide on Halloween Cyber Threats.